Understanding Distributed Denial of Service Attacks (DDoS)
The digital landscape has become increasingly complex and interconnected, making it a prime target for various cyber threats. One of the most concerning forms of these threats is the distributed denial of service attack, commonly referred to as a DDoS attack. This type of attack involves overwhelming a target's online services by flooding it with a massive amount of traffic, essentially crippling its ability to function properly. Organizations of all sizes have fallen victim to such attacks, leading to significant operational disruptions and financial losses.
As the prevalence of internet-connected devices grows, so does the potential for distributed denial of service (DDoS) attacks. Cybercriminals exploit vulnerabilities in networks and systems, coordinating attacks through large networks of compromised computers known as botnets. Understanding how these attacks work and their implications is critical for businesses and individuals alike. In this comprehensive article, we will explore the specifics of DDoS attacks, their impacts, and strategies for defense and mitigation.
What is a DDoS Attack?
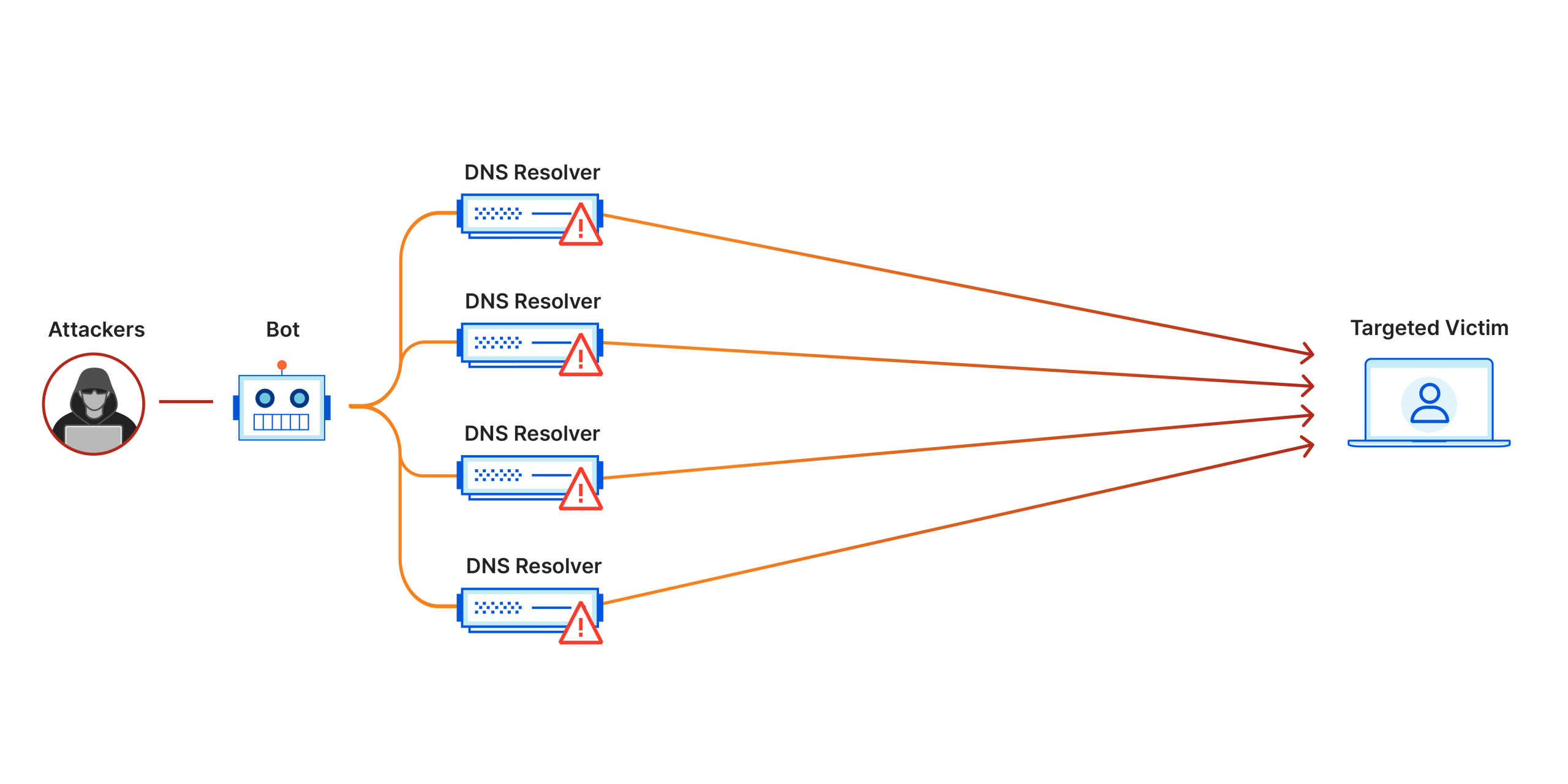
A distributed denial of service attack involves multiple compromised systems—often part of a botnet—coordinated to target a single system. The objective is to exhaust the resources of the target server or network, thereby denying legitimate users access to services. DDoS attacks are particularly insidious because they can originate from various points across the internet, making them difficult to fend off. Denial of service attacks, in general, come in many forms, but the distributed variant has grown in popularity as attackers discover the devastating effects they can have on businesses and infrastructure.
How DDoS Attacks Work
DDoS attacks function primarily through the collaboration of multiple compromised machines, often referred to as "zombies." These machines are infiltrated with malicious software that allows attackers to control them remotely. When an attack is launched, these zombie machines bombard the target with traffic requests. The overwhelming amount of requests can cause the service to slow down or, in severe instances, shut down entirely. This systematic flooding of data is what characterizes a DDoS attack, and its effects can be felt for hours or days after the initial attack.
Types of DDoS Attacks
There are several types of DDoS attacks, each employing different strategies to achieve their goal. Understanding these types can help organizations prepare for potential threats:
- Volume-based attacks: These attacks focus on saturating the bandwidth of the target, overwhelming it with sheer volume. The most common examples include ICMP floods and UDP floods.
- Protocol attacks: These attacks exploit weaknesses in network protocols, including SYN floods, which attack the transmission control protocol (TCP) to consume server resources.
- Application layer attacks: These attacks target specific features of applications, often designed to crash the server. Examples include HTTP floods, where the attacker sends seemingly legitimate requests that aim to overload the web server.
Commonly Used Techniques in DDoS Attacks
Attackers utilize a variety of techniques to carry out DDoS attacks with maximum effectiveness:
- Botnets: As previously mentioned, attackers create networks of compromised machines to launch coordinated attacks.
- Amplification: Attackers exploit protocols like DNS (Domain Name System) or NTP (Network Time Protocol) to amplify the volume of traffic sent to the target.
- Reflection: In this technique, attackers send requests to a publicly accessible server, which then sends the response to the target, further increasing the attack's volume.
The Impact of DDoS Attacks on Organizations
The consequences of a successful DDoS attack can be far-reaching and damaging. Organizations may suffer:
- Financial loss: Downtime leads to lost revenue, especially for online businesses.
- Reputation damage: Clients and customers may lose confidence in a business that is unable to protect its online services.
- Operational disruption: Employees may be unable to access necessary resources, leading to decreased productivity.
Notable DDoS Attack Incidents
Throughout history, several high-profile DDoS attacks have captured media attention and highlighted the vulnerabilities in various systems.
- Estonia (2007): One of the first major instances of a DDoS attack on a national scale, affecting numerous essential services, including government websites and banks.
- Dyn (2016): A massive attack on the DNS provider Dyn caused widespread outages for popular platforms like Twitter and Netflix, showcasing the potential impact of DDoS attacks on major services.
- GitHub (2018): GitHub experienced one of the largest recorded DDoS attacks, reaching a peak traffic volume of 1.35 terabits per second, demonstrating the evolving scale and sophistication of DDoS threats.
How to Defend Against DDoS Attacks
Defending against distributed denial of service attacks requires a multi-layered approach. Organizations can take proactive measures to safeguard their systems:
- Traffic analysis: Implementing tools that monitor incoming traffic can help identify abnormal patterns indicative of a DDoS attack.
- Over-provisioning resources: Ensuring that bandwidth and server capacity exceed expected traffic can help absorb attack traffic.
- DDoS mitigation services: Many organizations leverage professional DDoS protection services that specialize in filtering malicious traffic and maintaining service availability.
DDoS Mitigation Strategies
In addition to defensive measures, organizations should employ specific DDoS mitigation strategies to protect themselves effectively:
- Load balancing: Distributing incoming traffic across multiple servers can prevent any single server from becoming overwhelmed.
- Rate limiting: Implementing rate limits allows organizations to restrict the number of requests from a single IP or range of IPs, thereby reducing the impact of an attack.
- Geographical blocking: If attacks originate from specific geographic regions, organizations can implement blocks to mitigate the threat.
The Future of DDoS Threats
The rapidly evolving digital environment indicates that distributed denial of service (DDoS) attacks will continue to pose significant threats. As technology advances, so do the capabilities of attackers:
- Increased sophistication: Future attacks may employ more complex techniques, combining multiple attack vectors to overwhelm defenses.
- More targets: With the proliferation of Internet of Things (IoT) devices, attackers may have access to a larger pool of potential botnet participants.
- Ransom DDoS (RDoS): The evolving landscape of cybercrime may lead to the rise of RDoS where attackers threaten to launch DDoS attacks unless a ransom is paid.
Conclusion
Understanding distributed denial of service attacks is essential for anyone operating in the modern digital environment. As the cyber threat landscape continues to evolve, it's crucial for organizations to recognize the risks associated with these attacks and take proactive measures to mitigate their impact. By implementing effective defense and mitigation strategies, businesses can safeguard their operations and maintain service availability in the face of potential DDoS attacks.
Did you find this article helpful? Understanding Distributed Denial of Service Attacks (DDoS) See more here General.
Leave a Reply


Related posts